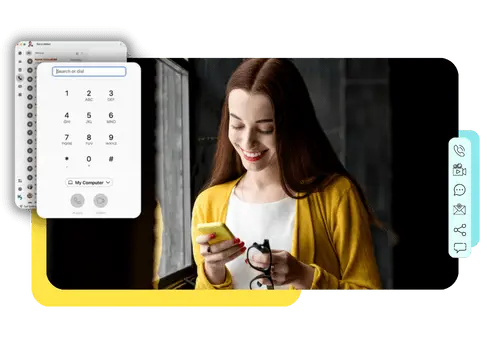
Your business never stops. Neither should your Phones.
Accelerate your business communications with one cloud-hosted phone system.
Our Solutions

One platform that does it all.
Spread your message to the world

Enterprise grade network solutions for your office
We provide support to thousands of customers.
0Min
Average Response Time
0%
1st Response Resolution
0%
Average Daily Close Rate

Kloud 7 is a Wonderful Company. Their response time is almost instant. Always fix any problem we have immediately. So professional and prompt. Would recommend it to everyone.

We are using Kloud 7 for our phone services and the entire team has been so helpful in training us on the new system and being so prompt anytime we need assistance. We have no complaints.

Kloud 7 continues to exceed our expectations! From customer care, service options and equipment to community involvement, Kloud 7 is by far the best provider we’ve ever worked with.
Enhanced Agility, More Productivity, Better Collaboration.
Integrate industry leading apps and softwares to optimize your business communications.

How can you bring endless utility to your business with Call Reporting Analytics?
Know your business like never before while tracking your growth and opportunities.
Please tell us a bit about yourself before we get started.